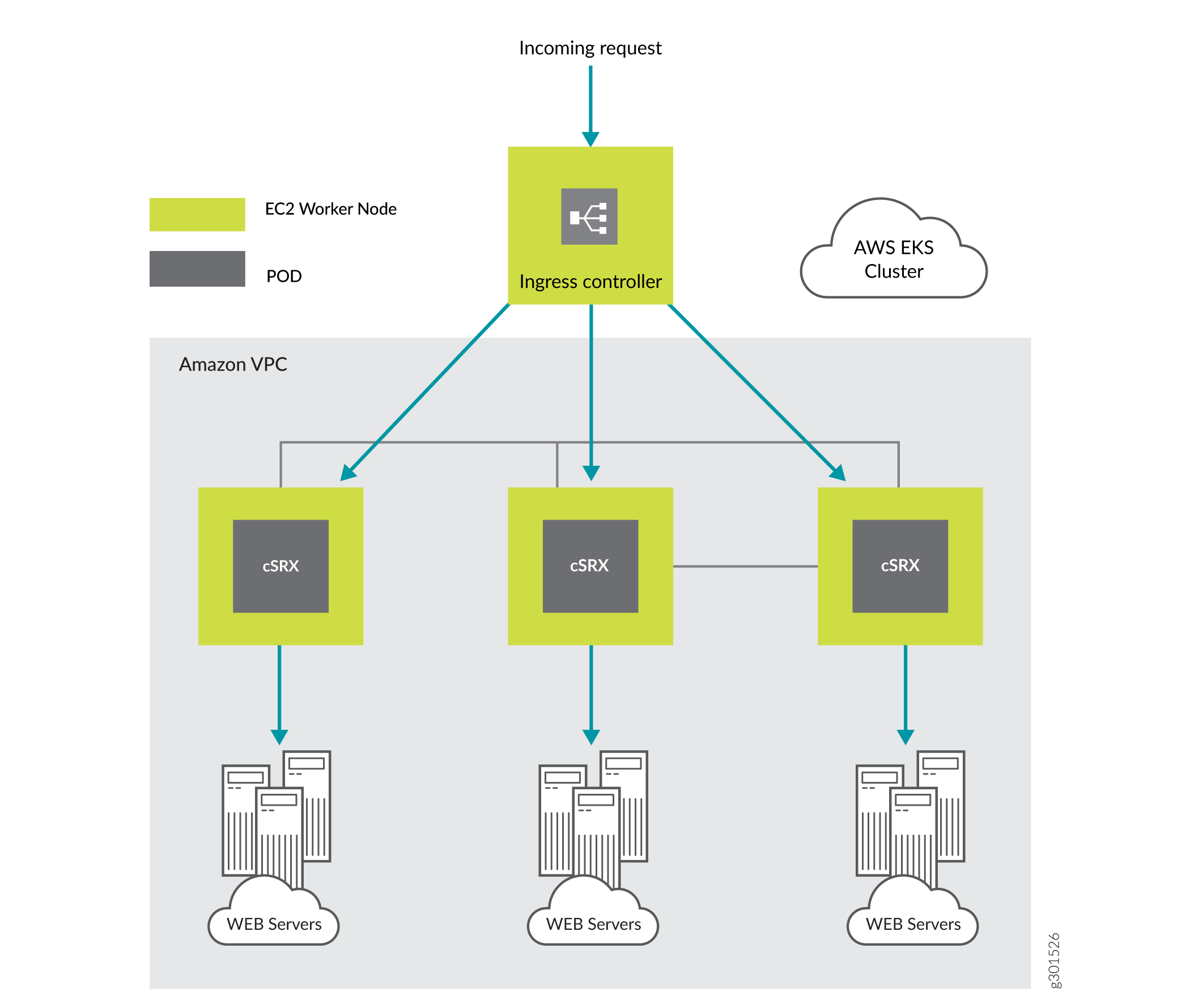
cSRX as a Service with Ingress Controller on AWS EKS | cSRX Deployment Guide for AWS | Juniper Networks TechLibrary
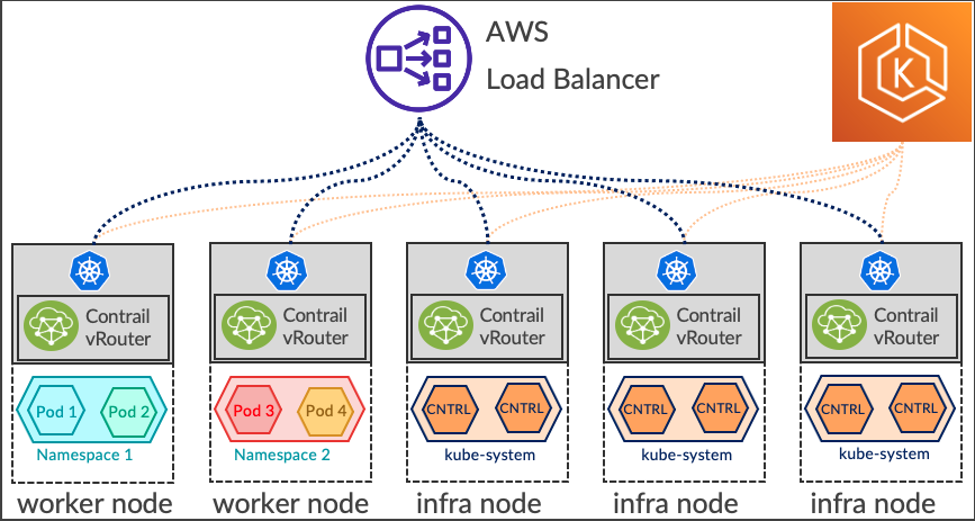
Juniper Brings Contrail's Virtual Networking to KubeVirt, Google Anthos and Amazon's EKS | Official Juniper Networks Blogs
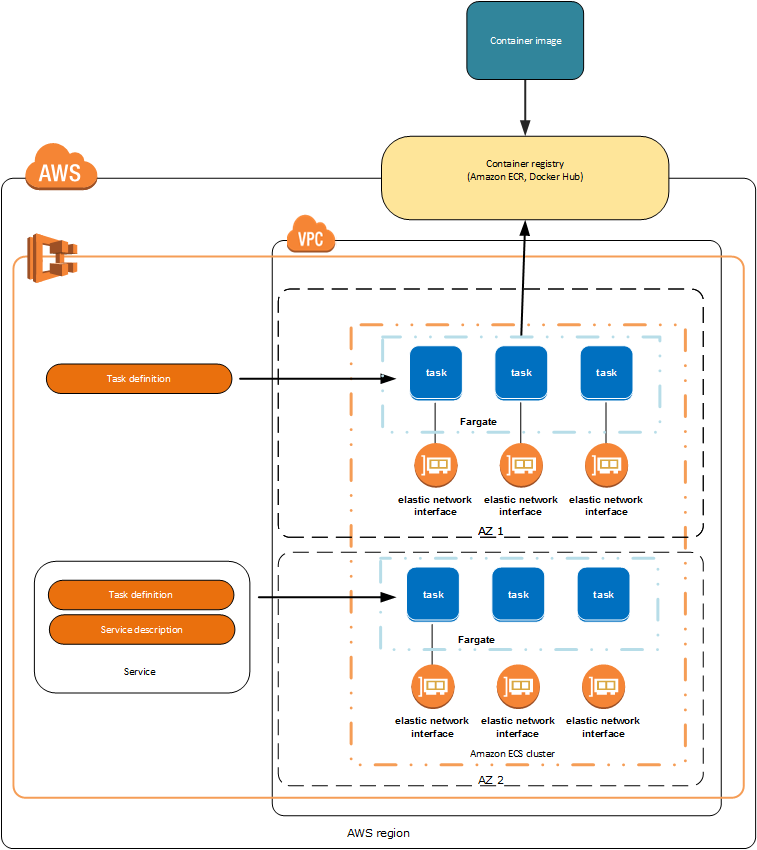
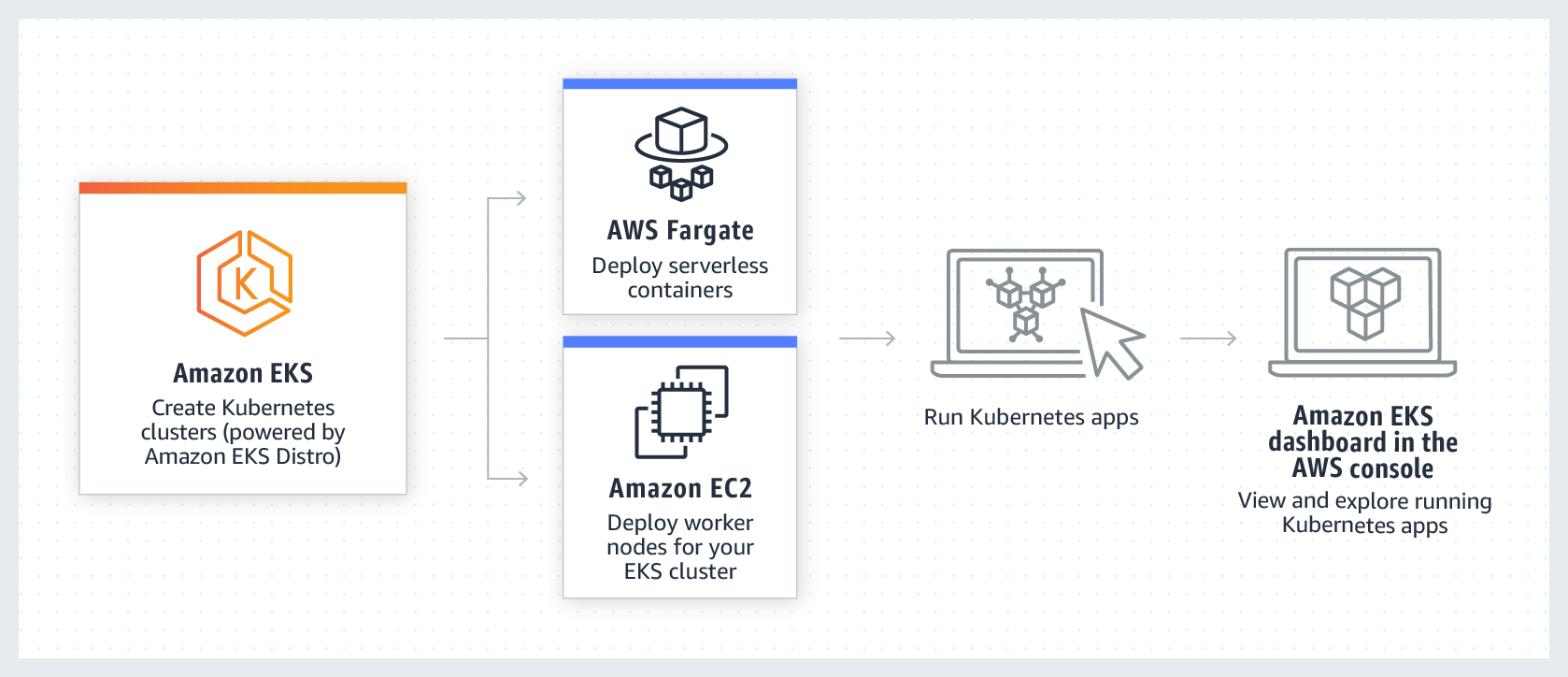
What, Why, How: Run Serverless Kubernetes Pods Using Amazon EKS and AWS Fargate - IOD - The Content Engineers

Securely Decoupling Kubernetes-based Applications on Amazon EKS using Kafka with SASL/SCRAM | Programmatic Ponderings

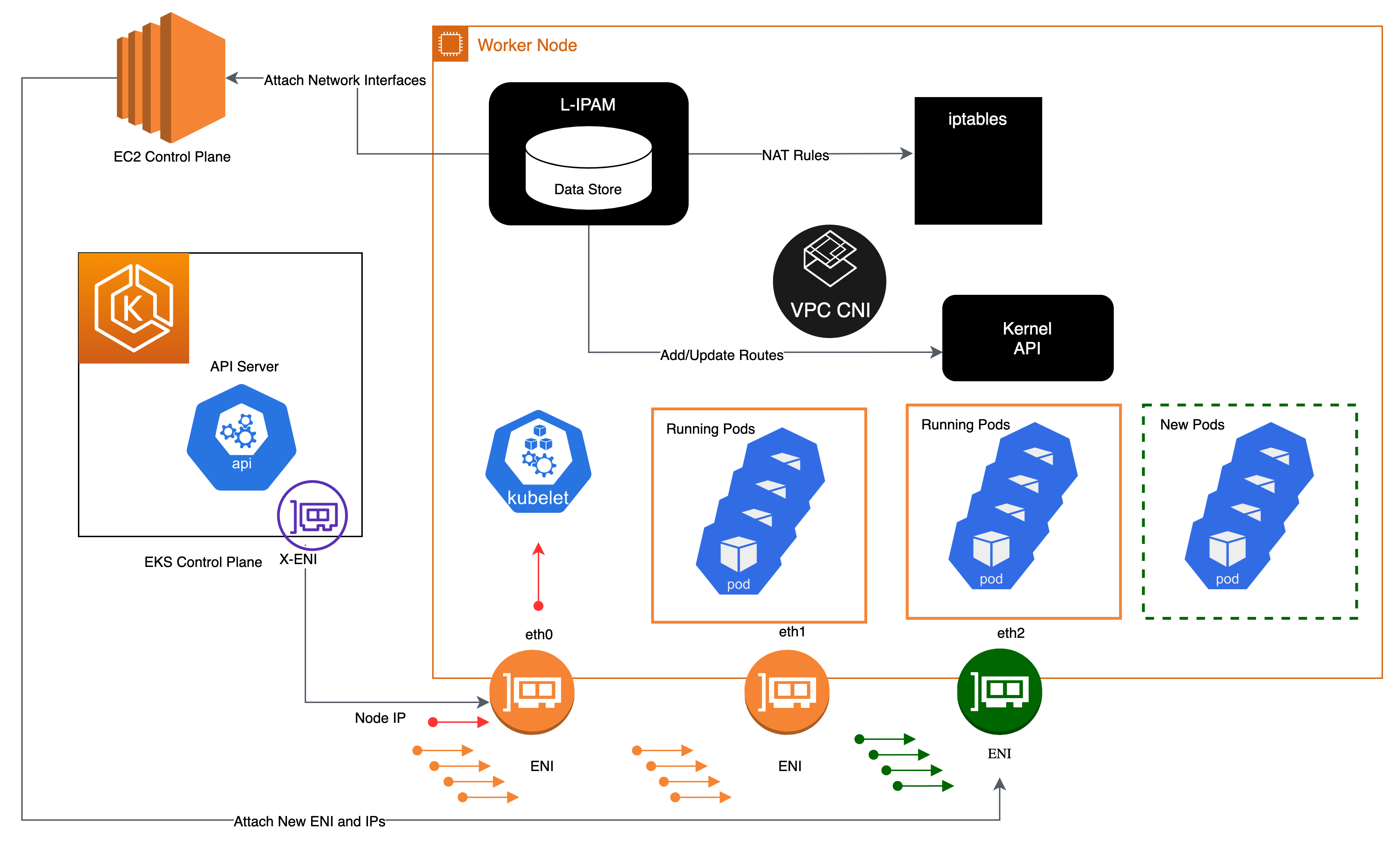
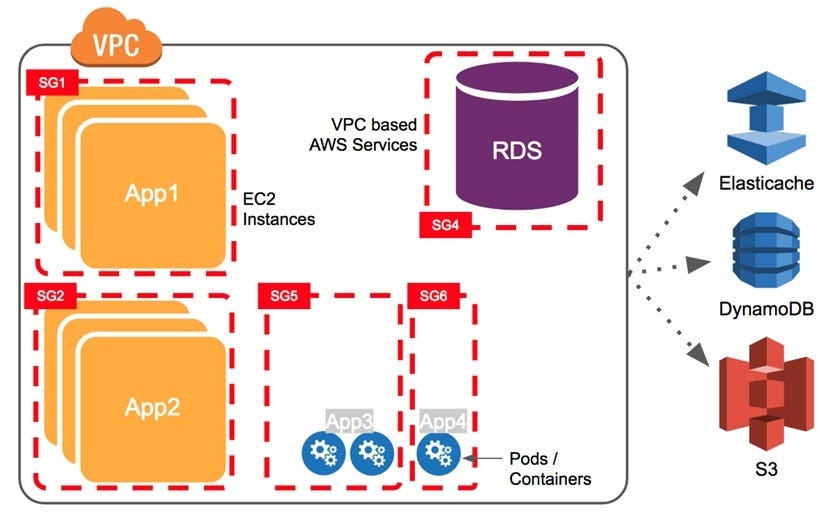
Combining IAM Roles for Service Accounts with Pod level Security Groups for a defense-in-depth strategy - DEV Community 👩💻👨💻
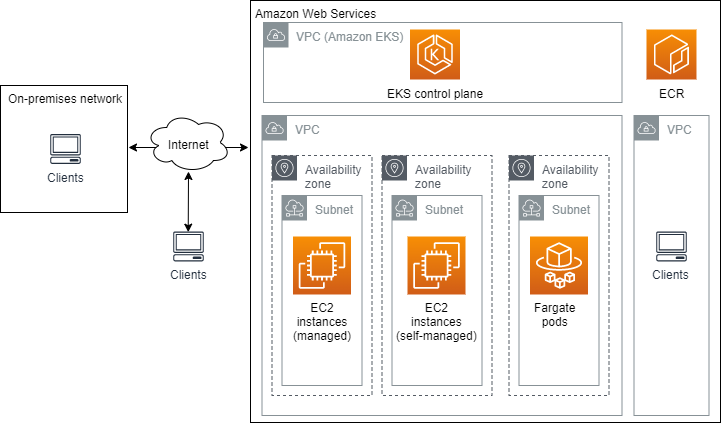
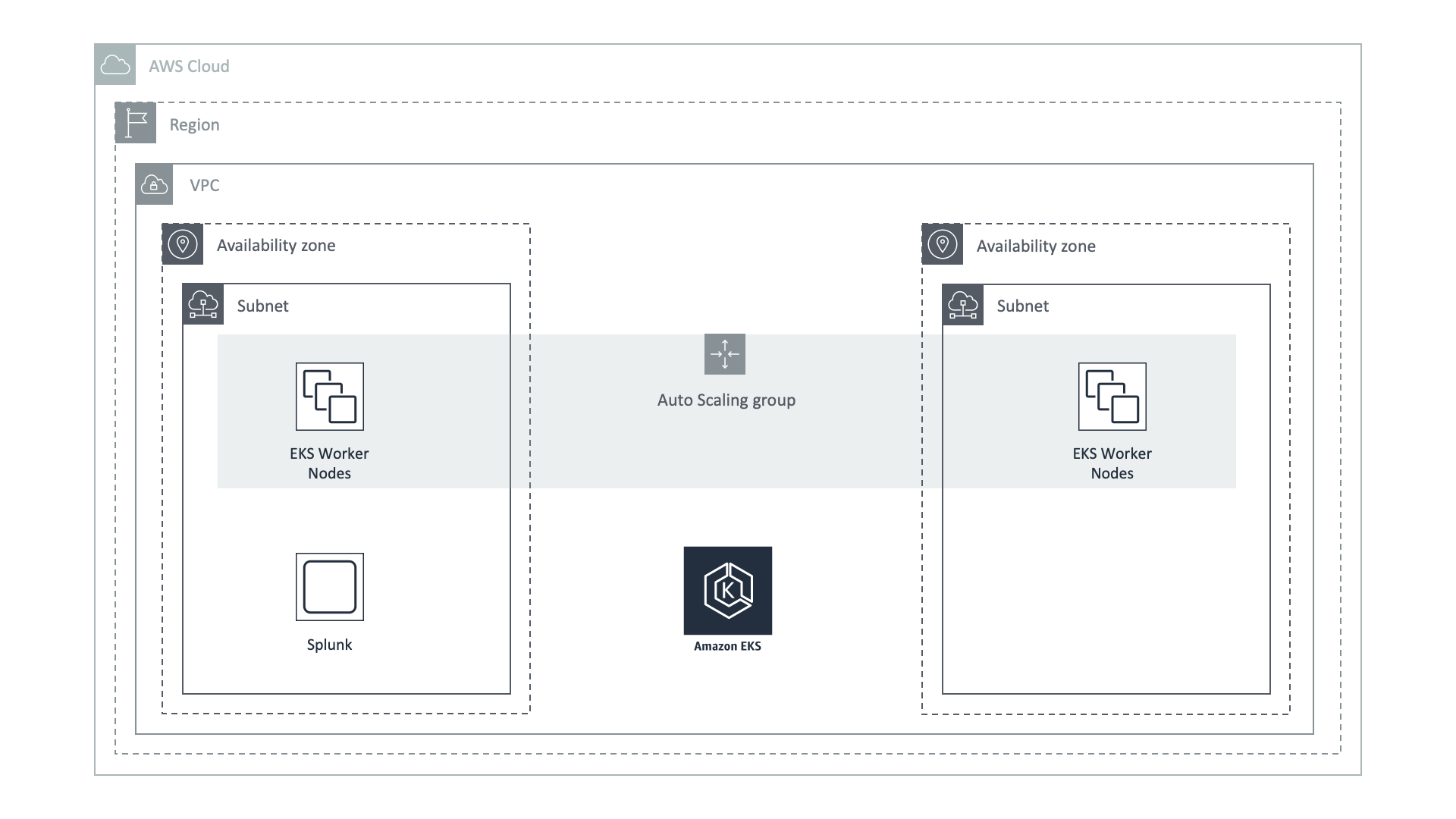
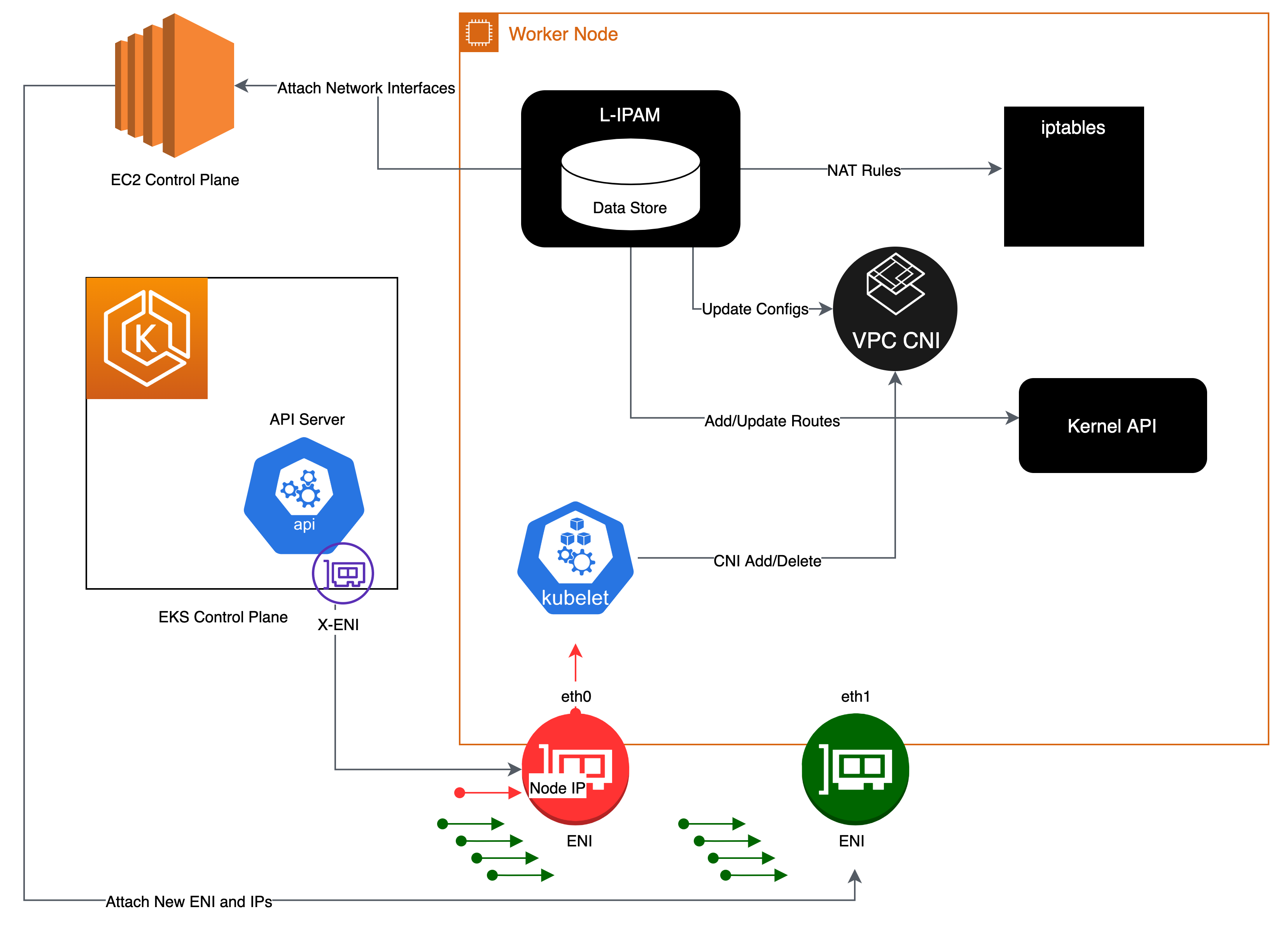
Amazon Elastic Kubernetes Service (Amazon EKS) Architecture Explained with Diagram - DevOpsSchool.com